In a world where data breaches can spell disaster for businesses, cloud data security is more important than ever. Entrepreneurs, in particular, need to ensure their data is well-protected to maintain customer trust and operational efficiency. This guide will walk you through everything you need to know about cloud data security, from understanding potential threats to implementing best practices and choosing the right cloud service provider.
Toc
Introduction to Cloud Data Security
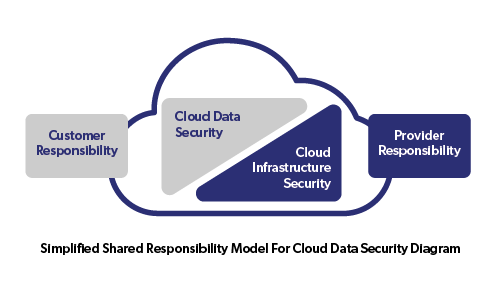
In today’s digital age, businesses are relying more and more on cloud computing to store, manage and process their data. With the rise of remote work and the increasing amount of sensitive information being stored online, it is crucial for entrepreneurs to prioritize cloud data security in order to protect their business and their customers.
What is Cloud Data Security
Cloud data security refers to a set of practices and technologies designed to protect data stored in cloud environments from unauthorized access, breaches, and other cyber threats. It encompasses a range of measures, including encryption, access controls, and regular security audits, to ensure that data remains confidential, integral, and available. By adopting robust cloud data security protocols, businesses can safeguard their sensitive information, mitigate risks, and comply with regulatory requirements.
Potential Threats to Cloud Data Security
Understanding the potential threats is the first step in implementing effective cloud data security. Some of the most common threats include:
- Data Breaches: Unauthorized access to sensitive information can lead to data breaches, resulting in financial loss, legal repercussions, and damage to company reputation.
- Malware and Ransomware: Malicious software can infiltrate cloud systems, corrupting data or locking users out until a ransom is paid.
- Insider Threats: Employees or contractors with access to data may intentionally or unintentionally cause security incidents.
- Account Hijacking: Attackers can gain control of user accounts through weak passwords or phishing attacks, leading to unauthorized access to data.
- Insecure APIs: Vulnerabilities within APIs can be exploited by attackers to gain access to cloud systems and data.
Why It’s Crucial for Entrepreneurs
For entrepreneurs, cloud data security is not just a technical concern but a business imperative. Small and medium-sized businesses often handle sensitive data such as customer information, financial records, and proprietary business plans. A data breach can have catastrophic consequences, including financial losses, legal penalties, and irreparable damage to customer trust. Moreover, entrepreneurs may not have the extensive resources that larger corporations possess to recover from such incidents, making preventive measures all the more critical. Securing cloud data effectively ensures business continuity, builds customer confidence, and provides a solid foundation for long-term growth.
Common Cloud Security Threats and Best Practices
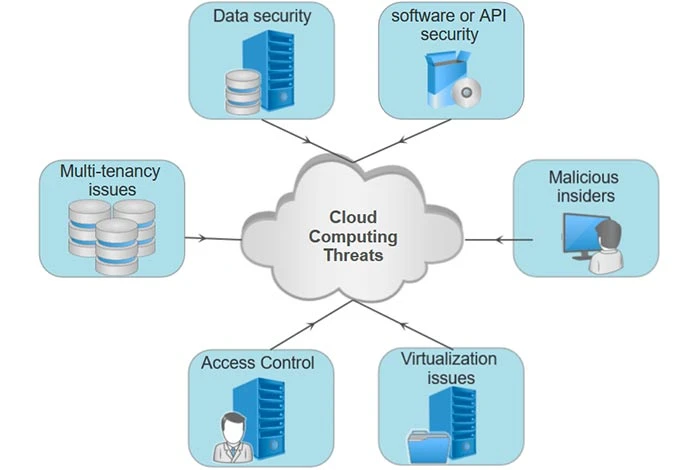
To protect your data from potential threats, it is essential to adopt best practices for cloud security.
Overview of Potential Risks
Understanding the landscape of cloud security threats is essential for any entrepreneur. Here are some common risks:
- Data Breaches: Unauthorized access to sensitive information can lead to severe financial and reputational damage.
- Malware Attacks: Malicious software can corrupt or steal data, disrupting business operations.
- Insider Threats: Employees with malicious intent or those who have been compromised can pose significant risks.
- Account Hijacking: Hackers can take over user accounts, gaining access to confidential data.
- Misconfiguration: Incorrectly configured cloud environments can leave critical data exposed.
Best Practices for Cloud Data Security
- Implement Strong Access Controls: Ensure that only authorized personnel have access to sensitive data, limit privileges to only what is necessary, and regularly review access permissions.
- Encrypt Data: Encryption transforms data into a code that can only be accessed with a decryption key, making it unreadable to unauthorized users even if they gain access.
- Regularly Backup Data: Regular backups ensure that in the event of a breach or disaster, your data can be restored quickly and easily.
- Train Employees on Security Awareness: Educate employees on best practices for data security, including password management, recognizing phishing attacks, and reporting suspicious activities.
- Choose Reputable Cloud Service Providers: Do your research and choose cloud service providers with strong security measures in place, transparent policies, and a track record of keeping customer data safe.
- Regular Security Audits: Conduct regular audits to identify vulnerabilities and address them promptly before they can be exploited.
Importance of Regular Audits and Updates
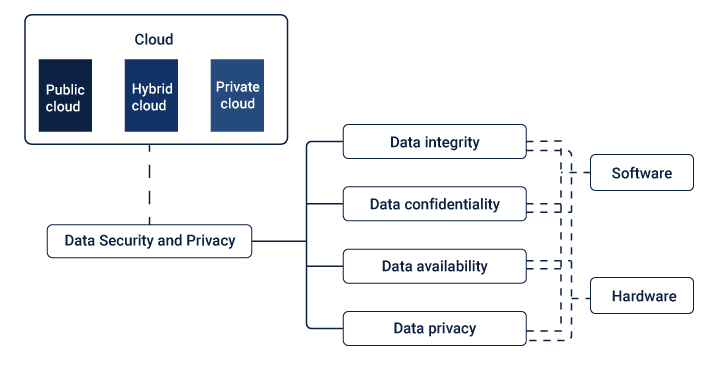
Regular security audits are crucial for maintaining cloud data security. They involve reviewing and testing all components of your cloud infrastructure, including networks, servers, applications, and data storage, to identify potential vulnerabilities or weaknesses. Regular updates ensure that any known security issues are addressed promptly and the latest security protocols are in place.
What are Security Audits and Updates
Security audits involve a systematic examination of an organization’s cloud infrastructure and policies to ensure that security measures are effectively protecting data. This process includes assessing access controls, configurations, software vulnerabilities, and adherence to compliance requirements.
Regular updates refer to the timely application of patches and updates to software and systems to address known vulnerabilities. This process ensures that any newly discovered security weaknesses are promptly fixed, thus minimizing the risk of exploitation by malicious actors. Keeping software up-to-date is a critical aspect of a robust cloud security strategy, as attackers often exploit outdated systems.
How to Conduct Security Audits
Conducting security audits involves several steps:
- Define the Scope: Determine which systems, applications, and data need to be audited.
- Assess Risks: Identify potential threats and vulnerabilities within the scope.
- Review Policies and Procedures: Ensure that your security policies and procedures are comprehensive and up-to-date.
- Test Controls: Conduct tests to verify the effectiveness of security controls in place.
- Report Findings: Document any vulnerabilities or areas of improvement identified during the audit.
- Implement Improvements: Take corrective actions to address the issues uncovered and enhance your security posture.
- Continuous Monitoring: Establish ongoing monitoring to detect and respond to new threats promptly.
By thoroughly evaluating and improving your cloud security measures, security audits can significantly enhance your organization’s ability to safeguard its data.
Benefits of Security Audits and Updates
- Identifying Vulnerabilities: Regular audits can help identify potential security gaps and address them before they can be exploited.
- Compliance: Many industries have regulatory requirements for data security, and regular audits can ensure compliance with these standards.
- Safeguarding Against New Threats: With the constant evolution of cyber threats, regular audits and updates are critical to stay ahead of new risks.
- Cost Savings: By identifying vulnerabilities early on, businesses can save significant costs associated with responding to a data breach or recovering from a costly cyber attack.
The Role of Encryption in Cloud Security

Encryption is the process of converting data into a code to prevent unauthorized access. In the context of cloud services, encryption ensures that even if data is intercepted, it remains unreadable without the decryption key. This makes it a fundamental part of any robust cloud security strategy.
The Role of Artificial Intelligence in Cloud Data Security
Artificial Intelligence (AI) is increasingly becoming a cornerstone in the field of cloud data security. By leveraging advanced machine learning algorithms, AI can provide a more proactive and sophisticated approach to identifying and mitigating threats. Here are some ways AI is enhancing cloud data security:
- Threat Detection and Response: AI systems can analyse vast amounts of data in real-time to detect anomalies and potential threats more effectively than traditional methods. This enables quicker response times and prevents potential breaches.
- Automated Security Measures: With AI, many security measures can be automated, reducing the need for manual intervention and thereby minimizing human error. Examples include automated patch management and real-time access control adjustments.
- Predictive Analytics: AI can predict potential vulnerabilities and threats before they occur by analysing historical data and recognizing patterns. This allows companies to address issues proactively rather than reactively.
- Enhanced User Authentication: AI-powered behavioural analysis can be used for more secure user authentication. By continuously monitoring user behaviour, AI can identify unusual activities and flag potential security issues.
- Incident Response: In the case of a security breach, AI can help streamline the incident response process through automation and by providing data-driven insights for quicker resolution.
Cloud Security Compliance and Standards
Adhering to industry standards and regulations is essential for maintaining cloud data security. Compliance not only ensures that a business meets legal and regulatory requirements but also fosters trust with customers and partners.
- ISO/IEC 27001: This international standard provides a framework for Information Security Management Systems (ISMS) and is one of the key standards for cloud security.
- GDPR: For businesses handling data of EU citizens, compliance with the General Data Protection Regulation is mandatory. GDPR emphasises data protection and privacy.
- HIPAA: Health Insurance Portability and Accountability Act compliance is crucial for healthcare organisations, ensuring that patient data is secured adequately.
- SOC 2: Service Organization Control 2 compliance focuses on the controls relevant to security, availability, processing integrity, confidentiality, and privacy, making it vital for organizations providing cloud services.
By aligning with these and other relevant standards, businesses can not only protect their data more effectively but also demonstrate their commitment to robust cloud security practices.
Choosing the Right Cloud Service Provider
Selecting a reliable and secure cloud service provider is crucial for ensuring the security of your data. When evaluating potential providers, here are some essential factors to consider:
Factors to Consider
When selecting a cloud service provider, consider the following factors:
- Security Features: Ensure the provider offers advanced security measures such as encryption, firewalls, and intrusion detection systems.
- Compliance: Verify that the provider complies with industry standards and regulations relevant to your business.
- Support: Opt for providers that offer robust customer support to assist you in managing and troubleshooting security issues.
- Transparency: Ensure that the provider is transparent about its security practices and provides regular updates on any changes or upgrades to their systems.
- Data Backup and Recovery: Choose a provider with reliable data backup and recovery processes in place to prevent data loss in case of a breach or system failure.
- Cost-effectiveness: While security should be a top priority, it’s essential to find a provider that offers cost-effective solutions within your budget.
Top Cloud Service Providers for Cloud Data Security
When it comes to cloud data security, some providers stand out for their robust security features, compliance with industry standards, and excellent support. Here are some of the top cloud service providers renowned for their commitment to data security:
- Amazon Web Services (AWS): AWS is a leader in cloud security, offering comprehensive security features including encryption, Identity and Access Management (IAM), and a wide range of compliance certifications. Their security services are designed to meet the most stringent regulatory requirements.
- Microsoft Azure: Azure provides a suite of security tools and services including Azure Security Center and Azure Active Directory. They ensure compliance with numerous global standards like ISO/IEC 27001, GDPR, and HIPAA. Their robust security infrastructure helps in safeguarding data against emerging cyber threats.
- Google Cloud Platform (GCP): Google Cloud prioritizes security with features such as encryption at rest and in transit, advanced threat detection, and extensive compliance certifications. Google’s AI and machine learning capabilities also enhance their security offerings by providing advanced threat analytics.
- IBM Cloud: IBM Cloud offers a trusted security framework with features like data encryption, secure access controls, and compliance with standards such as GDPR and HIPAA. Their integrated security solutions provide comprehensive protection for enterprise data.
- Oracle Cloud Infrastructure (OCI): OCI focuses on strong security for cloud environments with features such as data encryption, Virtual Cloud Networks (VCNs), and compliance with various international standards. Their dedicated security zones enhance data protection and threat prevention.
Conclusion

Choosing the right cloud service provider is just one piece of the puzzle when it comes to ensuring comprehensive data security. Equally important is the ongoing management and monitoring of your cloud environment. Here are some best practices to help maintain cloud security:
- Regularly review and update your security policies and procedures.
- Implement multi-factor authentication for added protection against unauthorized access.
- Conduct regular vulnerability assessments and penetration testing to identify potential weaknesses in your system.
- Monitor user activity and data usage to detect any unusual or suspicious behavior.
By following these best practices, along with choosing a reliable cloud service provider, businesses can mitigate the risks associated with cloud data security and ensure the safety of their valuable data. So, it is crucial for organizations to prioritize cloud data security as part of their overall information security strategy to protect their sensitive data from ever-evolving cyber threats.












